Microsoft 365 Inventory Tool
Microsoft 365 is like the attic nobody dares to open. Ghost Teams, forgotten SharePoints, and abandoned OneDrives packed with files from people long gone. IT shows up to clean the mess with a flashlight, only to regret it fast. 1Security’s Inventory Tool brings order—consolidating accounts, permissions, and resources into one dashboard.

Benefits
1Security helps your team work faster and safer in Microsoft 365: ready for AI, protected against breaches, audit-ready for compliance, and prepared to recover quickly from any incident.
Risk reduction
Monitor accounts, permissions, and activity across Microsoft 365.
Maintain compliance
Generate audit-ready reports aligned with GDPR, ISO 27001, and HIPAA.
Business continuity
Prevent excess inventory of abandoned sites or inactive users before they become security liabilities.
Time savings
Replace manual scripts and siloed admin centers with a single inventory management software.
Clarity
Real-time visibility into accounts, inventory levels, and permissions across the tenant.
Confidence
Streamline investigations, review changes, and optimize inventory operations with full context.
Capabilities
1Security turns scattered accounts, outdated permissions, and abandoned workspaces into a clean, complete, and always up-to-date inventory. No more guessing. No more cleaning up after incidents. Just control.
Unified Inventory Dashboard
1Security provides a centralized inventory management solution across SharePoint, OneDrive, Microsoft Teams, and other Microsoft 365 services. Admins gain a clear overview of accounts, permissions, and resources — eliminating manual tasks and streamlining the inventory process.
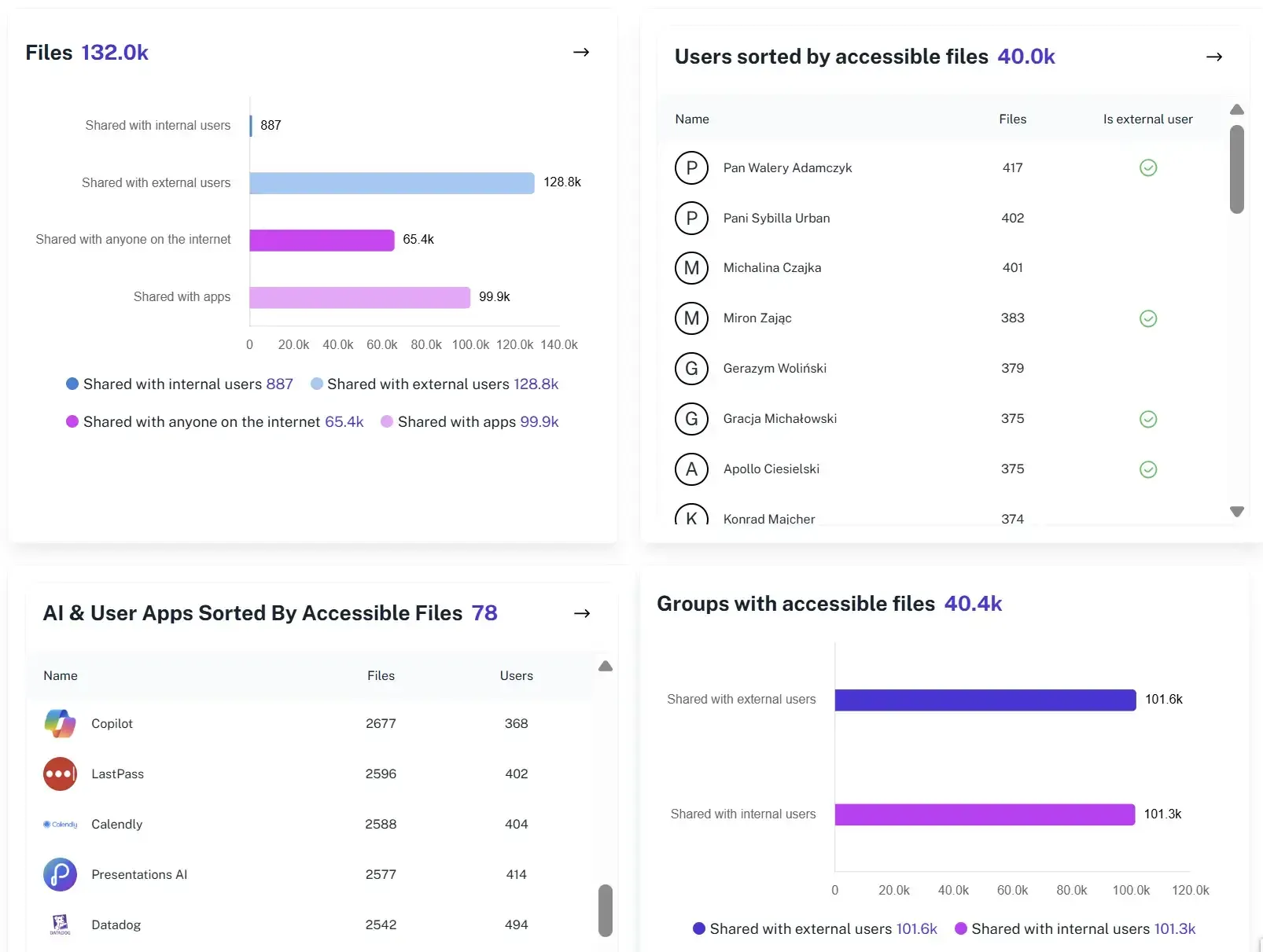
Permissions Visibility
See who has access to what across your Microsoft 365 system. Quickly identify inactive accounts, over-privileged users, or external guests still connected to sensitive sites. This level of control ensures your inventory operations remain secure.

Real-Time Alerts on Inventory Risks
Gain real-time visibility into abandoned Teams, orphaned OneDrive accounts, and SharePoint sites containing sensitive files. Alerts highlight risks such as oversharing or external users with access, so security teams can take control before issues escalate.

Activity Tracking and Reporting
Track inventory data such as permission changes, account activity, and sensitive file access across Microsoft 365. Instead of exporting CSV files from different admin centers, 1Security provides audit-ready reports that streamline compliance, investigations, and operational efficiency.

AI Readiness Checks
As organizations prepare for Copilot, 1Security prevents customer dissatisfaction by surfacing sensitive files, inactive resources, and risky configurations that AI might expose. This helps companies maintain optimal stock levels of access — ensuring Copilot adoption enhances collaboration without increasing risk.

Inventory “Time Travel”
Unique to 1Security, time travel lets admins roll back permissions and access to a previous safe state. Instead of reacting to errors, you can restore inventory processes exactly as they looked before a risky change or incident.

Audyt gotowości Copilot
Przed wdrożeniem Microsoft Copilot zweryfikuj etykiety, zasady linków i granice dostępu, aby AI widziało tylko to, co powinno. Zidentyfikuj wrażliwe dane, które Copilot mógłby ujawnić w SharePoint Online, Exchange Online, OneDrive for Business i Microsoft Teams, i najpierw zamknij luki.

Security You Can Trust
1Security is built with enterprise-grade protection. We are ISO 27001 certified, fully GDPR compliant, and host all customer data in secure European data centers. Your sensitive information remains private, protected, and audit-ready.

Security & Compliance
1Security ensures your Microsoft 365 inventory isn’t just visible—it’s verifiable, defensible, and ready for every audit. Compliance needs proof, not assumptions. 1Security keeps your Microsoft 365 inventory audit-ready. Request a demo today.
"With 1Security’s inventory monitoring, we finally know which accounts and sites are active, and which should be archived. It turned what used to take weeks into a single dashboard view."
Microsoft 365 Admin, Higher Education"1Security gives us confidence before every audit. The ability to see inactive accounts and abandoned sites across Microsoft 365 saved us from a compliance nightmare."
IT Security Manager, Financial Services"Before 1Security, our Microsoft 365 inventory was guesswork. Now we know exactly which accounts are active, which are abandoned, and who has access to what—without wasting days on manual checks. It’s like flipping on the lights in a dark room."
Head of IT Operations, ManufacturingWho Benefits Most?
1Security supports organizations of all sizes — from highly regulated industries to fast-growing mid-size firms.
Works seamlessly with your ecosystem
1Security connects natively with the tools you already use — giving you full visibility and control without adding complexity.
Popular Use Cases
See how organizations use 1Security to create audit-ready reports, track access history, streamline preparations across distributed admin centers, and present defensible evidence.
Frequently asked questions
Everything you need to know about the product.
How does 1Security detect abandoned accounts or sites?
1Security flags inactive users, orphaned OneDrive accounts, and Teams/SharePoint sites with no recent activity — giving admins the context to archive or remove them.
Can 1Security track external guest access across the inventory?
Yes. Guest accounts and external users are visible in the unified inventory, so you can see who still has access and remove them if needed.
How does the rolling back feature work for inventory?
When changes or incidents occur, 1Security lets you restore account and permission settings to a previous state — simplifying incident recovery and audits.
Isn’t Microsoft’s native reporting enough?
Native tools provide valuable data but are fragmented across SharePoint Online, Exchange Online, Entra ID, Teams, Purview and Graph API. 1Security consolidates inventory, permissions, sensitivity, and activity signals into one place with audit-ready reporting.
Do you support ISO 27001, SOC 2, HIPAA, and GDPR work?
Yes. 1Security maps findings and evidence to common control frameworks, helping organizations demonstrate compliance more efficiently.
Does this replace Microsoft Purview, DLP, or Defender?
No. 1Security complements Microsoft’s ecosystem by adding context and workflows — the who, what, where, and why — and pairing it with remediation and compliance-ready evidence.
Can non-technical stakeholders use it?
Yes. Plain-language reports and read-only views make it easy for compliance, legal, and business stakeholders to see the evidence behind findings without needing admin rights.
Is this only for large enterprises?
No. While designed for complex environments, 1Security is equally valuable for mid-sized organizations running Microsoft 365 or Office 365 that need strong visibility into access, activity, and compliance.

Gain visibility. Ensure compliance. Boost productivity.
Stop guessing who has access to your sensitive data. With 1Security, you gain the visibility, automation, and confidence needed to protect your Microsoft 365 environment.










