Office 365 Access Management
Microsoft 365 permissions don’t explode—they pile up. Guests that never leave, files marked “public” by mistake, and forgotten external users that still have access. 1Security’s Access Management Tool untangles the mess, showing exactly who can see what—simple, safe, and audit-ready.

Why access management matters?
1Security helps your team work faster and safer in Microsoft 365: ready for AI, protected against breaches, audit-ready for compliance, and prepared to recover quickly from any incident.
AI Readiness
Safely deploy Copilot and other AI assistants without risking sensitive data exposure.
Save Admin Time
Eliminate "Excel-driven" manual access reviews; free up IT teams for strategic tasks, with scalability to support larger organizations and their complex access needs.
Reduce Risk of Data Breaches
Prevent unauthorized access and minimize insider threats with least privilege enforcement, enabling secure access to sensitive data across all environments.
Simplify Compliance
Demonstrate control for ISO 27001, GDPR, HIPAA, SOX, and other frameworks with audit-ready reporting, supporting regulatory compliance requirements.
Recover Faster from Incidents
Use forensic analysis to understand what happened and restore permissions in minutes, not weeks.
Evidence & remediation
Export evidence in one click and act immediately with guided fixes like link removals or guest expiration.
Capabilities
Replace blind spots with clarity. 1Security’s Office 365 Access Management Tool shows exactly which users, apps, and external guests have access to sensitive data — giving you one source of truth for every permission in Microsoft 365.
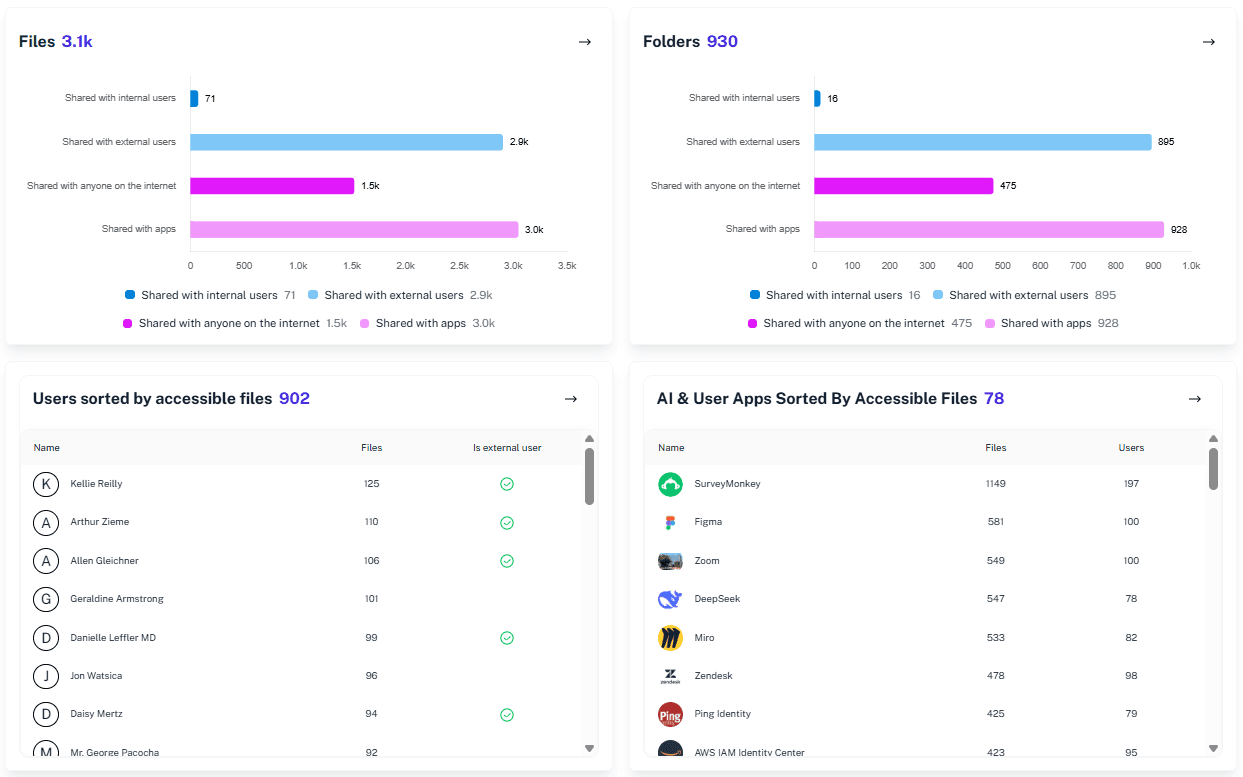
Access Visibility Dashboard
Instantly see which users, groups, and applications have access to sensitive files, SharePoint sites, Teams, and Exchange resources.
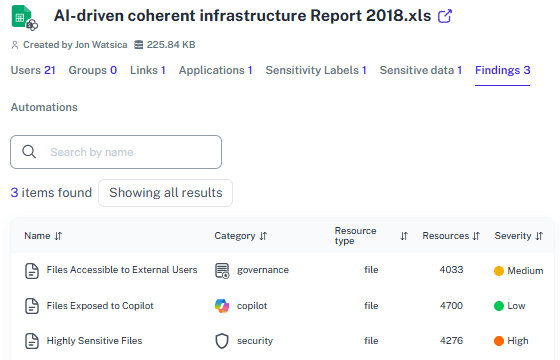
Sensitive Data Mapping
Go beyond Purview and identify who has access to your confidential data (e.g., credit card numbers, payroll, personal data) and who can access it, be it users, apps, Copilot, or other AI agents.

Permissions Monitoring & Alerts
Track access rights, monitor privileged permissions and requests managed through the admin center, and respond to risky behaviors.
Forensic Time Machine
Roll back to past permission states to investigate incidents and recover from data breaches. (soon to be released!)

Automated Policies
Remove risky external links, enforce expiration of guest accounts, manage external access and guest user permissions, and enforce conditional access for both internal and external access scenarios to streamline permission management.

AI & App Access Control
Ensure Microsoft Copilot and third-party apps only see the data they should, preventing unintended leaks.

Security You Can Trust
1Security is built with enterprise-grade protection. We are ISO 27001 certified, fully GDPR compliant, and host all customer data in secure European data centers. Your sensitive information stays private, protected, and audit-ready.

Security and Compliance
Stop guessing access, start governing it—centrally, continuously, and with evidence. Request a Demo of 1Security today!
"With 1Security, we finally understood who has access to what in our Microsoft 365 environment. What used to take days of manual checks is a 5-minute task with 1Security."
IT Security Director, Global Bank"The ability to simulate Copilot access before rollout saved us from exposing client data. This tool is a must for AI readiness."
CTO, Consulting Company"Offboarding stopped being guesswork. 1Security showed every SharePoint site, Team, and app a user touched, so we could close access in minutes—and prove it."
Head of IT, European UniversityWho Benefits Most?
1Security supports organizations of all sizes – from highly regulated industries to fast-growing mid-size firms.
Works seamlessly with your ecosystem
1Security connects natively with the tools you already use — giving you full visibility and control without adding complexity.
Popular Use Cases
See how organizations use 1Security every day — from preparing for Microsoft Copilot to streamlining audits, secure offboarding, and rapid incident response.
Frequently asked questions
Everything you need to know about the product.
Can 1Security replace our existing DLP or compliance tools?
No – it complements them. Tools like Microsoft Purview or Varonis protect data but require you to guess what should be protected. 1Security shows you where sensitive data is and who has access before you set policies. It also enhances your access management IAM strategy by providing visibility into digital identities and supporting regulatory compliance requirements.
What makes 1Security different from Microsoft Entra ID (Azure AD)?
Microsoft provides basic identity and access controls, but lacks real visibility into who actually has access to which files, sites, and data. 1Security fills this gap with a detailed, user-friendly map of permissions across Microsoft 365, including sensitive data locations and historical changes so you can govern AI and human access confidently.
How fast can we get started?
Most teams are onboarded within days. You can start with a demo environment, then connect your Microsoft 365 tenant securely to see access insights immediately. As part of onboarding, you can connect your Azure AD tenant, support hybrid identity scenarios with on premises Active Directory, and integrate with your on premises directory or Azure resources.
How does 1Security help manage different identity types, such as users, devices, and applications?
1Security supports a wide range of identity types, including user, device, application, and hybrid identities. It integrates with managed identities and Microsoft Entra Workload identities, enabling secure automation and access for services and applications across your environment.
Does 1Security integrate with advanced security features like privileged identity management and conditional access policies?
Yes. 1Security works alongside privileged identity management (PIM), conditional access policies, and access policies in Microsoft 365 and Azure AD. It provides visibility into privileged roles, helps enforce access policies, and supports granular control over who can access sensitive resources.
What is the role of Microsoft Entra admin center and Microsoft Entra Private Access in managing secure access?
The Microsoft Entra admin center serves as a centralized platform for managing device identities, application integrations, and workload identities. Microsoft Entra Private Access enables secure connectivity to private apps and Azure resources, providing seamless network access without relying on traditional VPNs. 1Security integrates with these tools to enhance secure access management.
Do you support ISO 27001, SOC 2, HIPAA, and GDPR work?
Yes. 1Security maps findings and evidence to common control frameworks, helping organizations demonstrate compliance more efficiently.
Is this only for large enterprises?
No. While designed for complex environments, 1Security is equally valuable for mid-sized organizations running Microsoft 365 or Office 365 that need strong visibility into access, activity, and compliance.

Gain visibility. Ensure compliance. Boost productivity.
Stop guessing who has access to your sensitive data. With 1Security, you gain the visibility, automation, and confidence needed to protect your Microsoft 365 environment.










