MS 365 inventory visibility
Microsoft 365 is full of valuable data—but over time, files, permissions, and guests pile up faster than anyone can track. Data only creates value when it’s organized, visible, auditable, and secure. You wouldn’t keep thirty years of receipts on your desk; 1Security brings clarity to your digital workspace, making your data work for you while keeping your organization safe.
What is the challenge?
Doing It with 1Security
Eliminate blind spots and regain control. 1Security delivers unified inventory visibility across Microsoft 365–so admins, security teams, and executives can see what exists, who can access it, and where sensitive data lives. You get meaningful insights, real-time alerts, and simplified management actions–all in a single pane of glass.
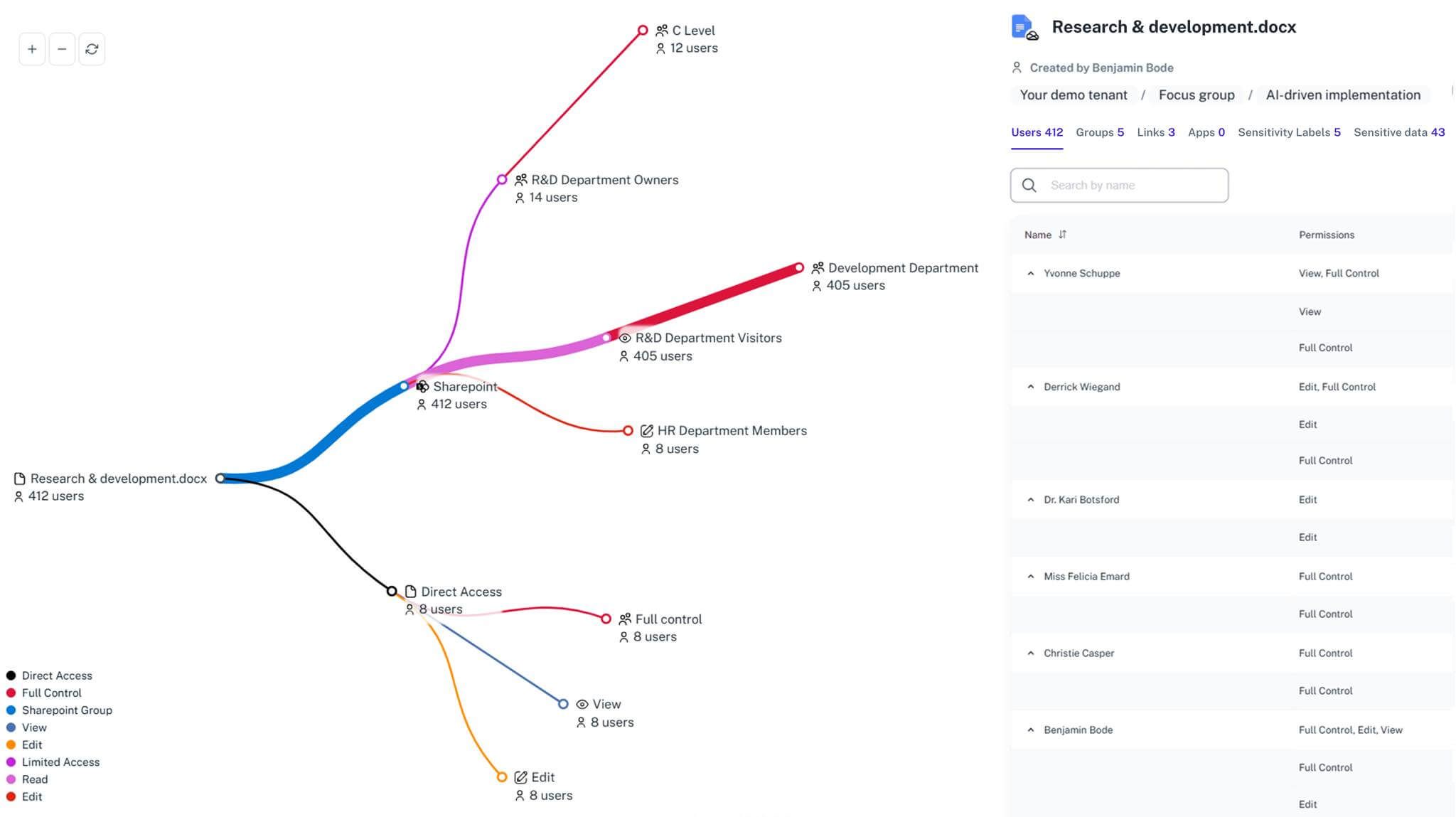
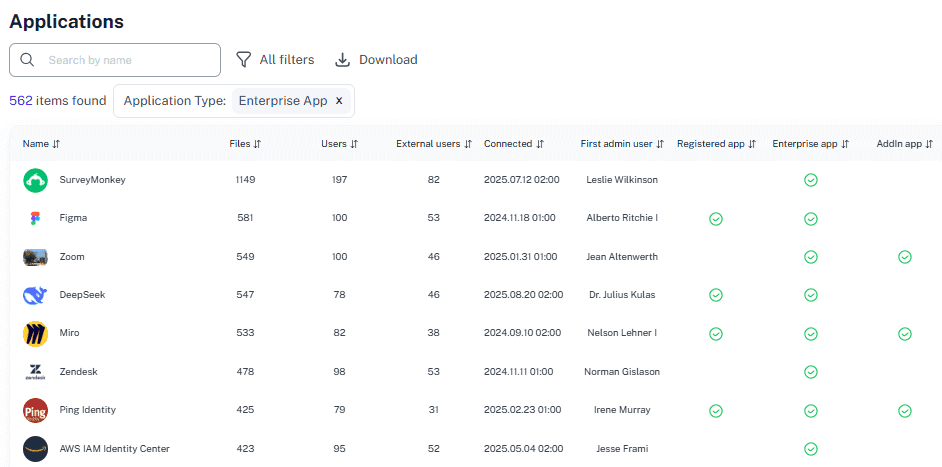
Unified Inventory View
Map Teams, SharePoint sites, and OneDrive in one dashboard with full visibility of users, memberships, and permissions.

Real-Time Change Detection
Detect permission drift, new external users, or “Anyone” links instantly with alerts that keep your data secure.

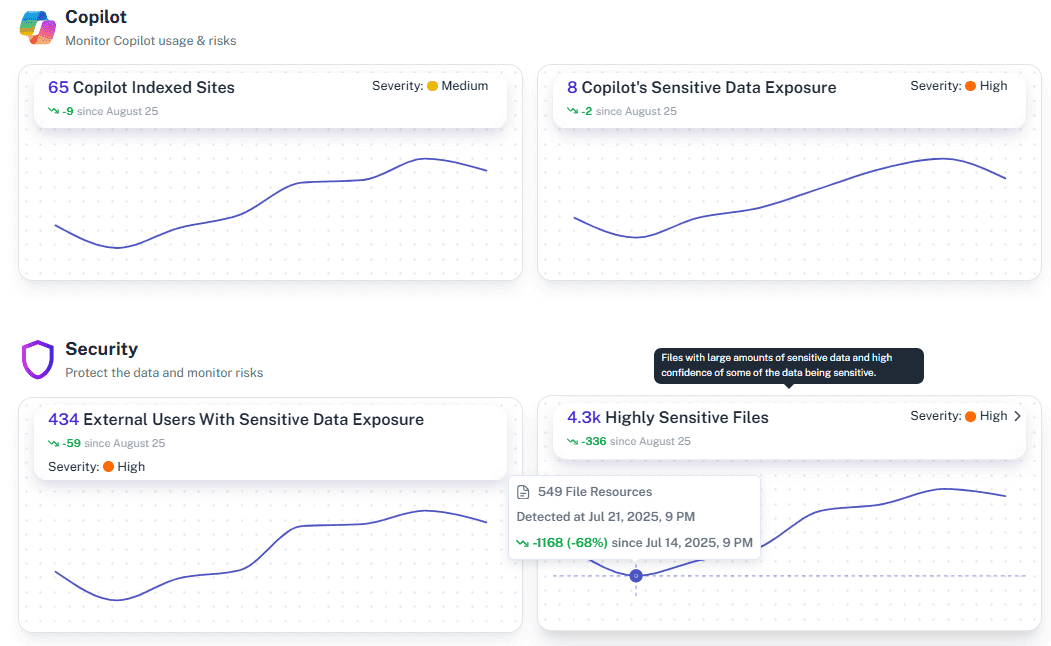
Sensitive Data Mapping
Merge Purview labels and permission data to reveal exposed confidential files and reduce oversharing across Microsoft cloud.

AI Readiness Check
See exactly what Copilot or third-party AI tools can access before rollout–ensuring a secure, responsible deployment.
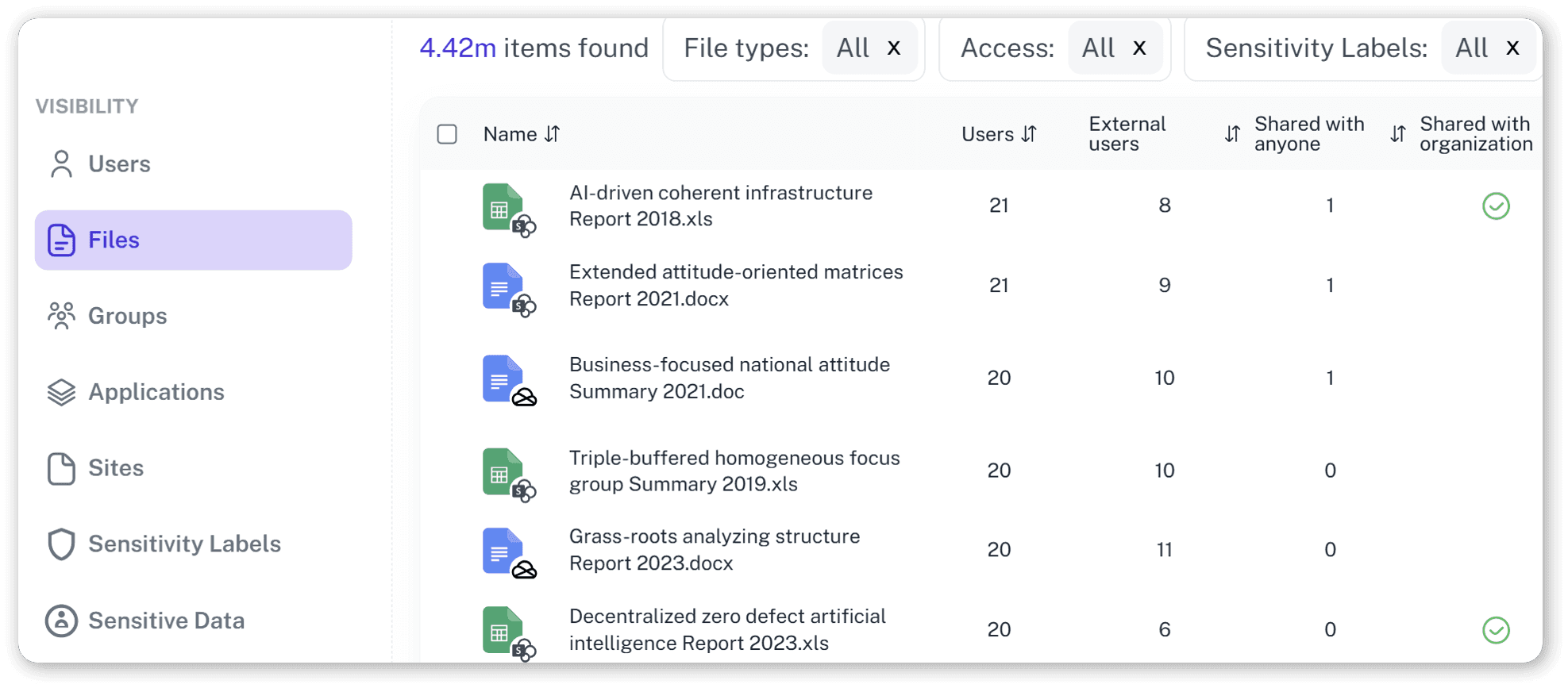
Audit-Ready Reports
Generate detailed information on permissions and changes over time. Simplify complex tasks into clear, actionable reports.
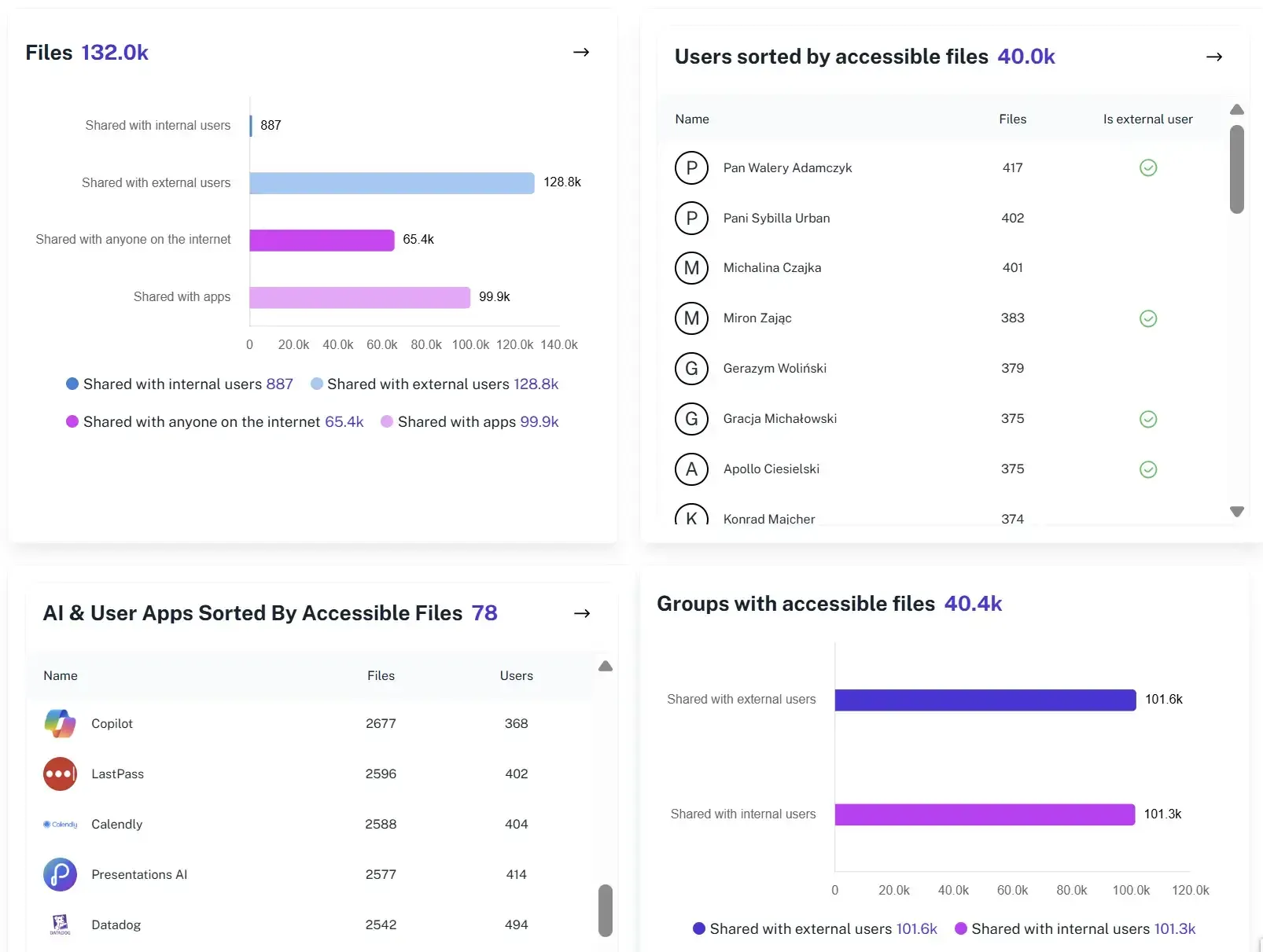
Clean-Up Insights
Identify unused Teams, SharePoint sites, or OneDrives safely. Retire inactive resources and improve environment efficiency.
Cross-Platform Integration
Combine alerts from Purview, Defender, and DLP with permission context for faster investigation and smarter decisions.
Solving It with Other Methods
Many organizations try to manage visibility using native Microsoft tools or manual audits–but these methods collapse under real-world scale.
Why Microsoft 365 Visibility Matters?
1Security gives you complete, connected visibility into Microsoft 365–revealing what exists, what’s sensitive, and who can access it. You gain control over data exposure, simplify compliance, and prepare your organization for safe AI adoption.
"Before 1Security, preparing for audit reviews meant weeks of spreadsheets. Now we generate evidence packs in minutes – auditors appreciate the clarity."
Compliance Manager, Global Insurance Firm"With 1Security’s compliance reporting, we can finally prove control. Every permission change is tracked; reports are exportable – no surprises during ISO or GDPR reviews."
Director of IT Compliance, Public University"With 1Security’s inventory monitoring, we finally know which accounts and sites are active and which should be archived – all in a single dashboard view."
Microsoft 365 Admin, Higher EducationWho Benefits Most?
1Security supports organizations of all sizes — from highly regulated industries to fast-growing mid-size firms.
Works seamlessly with your ecosystem
1Security connects natively with the tools you already use — giving you full visibility and control without adding complexity.
Frequently asked questions
Everything you need to know about the product.
Can 1Security track permission changes over time?
Yes. Every permission change is logged with time-stamped history, so you can review who accessed what and when–ideal for audits and investigations.
Does 1Security alert us about risky changes automatically?
Yes. 1Security monitors permission drift, external sharing, and “Anyone” links in real time–sending alerts so your team can respond before issues turn into incidents.
How does 1Security help during an incident or data leak?
It shows who had access, what was exposed, and when the change happened–enabling faster containment and evidence-backed response.
Does 1Security have access to our actual files or emails?
No. 1Security connects with the Microsoft 365 tools you already use–analyzing only metadata, permissions, audit signals, and sensitivity labels.
Can 1Security handle large Microsoft 365 tenants?
Yes. 1Security scales to hundreds of thousands of users and sites, running continuous inventory syncs without performance impact on your environment.
Do you support ISO 27001, SOC 2, HIPAA, and GDPR work?
Yes. 1Security maps findings and evidence to common control frameworks, helping organizations demonstrate compliance more efficiently.
Can non-technical stakeholders use it?
Yes. Plain-language reports and read-only views make it easy for compliance, legal, and business stakeholders to see the evidence behind findings without needing admin rights.
Is this only for large enterprises?
No. While designed for complex environments, 1Security is equally valuable for mid-sized organizations running Microsoft 365 or Office 365 that need strong visibility into access, activity, and compliance.
Gain visibility. Ensure compliance. Boost productivity.
Stop guessing who has access to your sensitive data. With 1Security, you gain the visibility, automation, and confidence needed to protect your Microsoft 365 environment.










