Office 365 OneDrive Monitoring with 1Security
"Anyone” links, forgotten guests, orphaned OneDrives, and audit logs no one wants to read — OneDrive makes it too easy to lose control. 1Security cuts through the chaos, showing who has access, what’s exposed, and where policy drift puts you at risk.
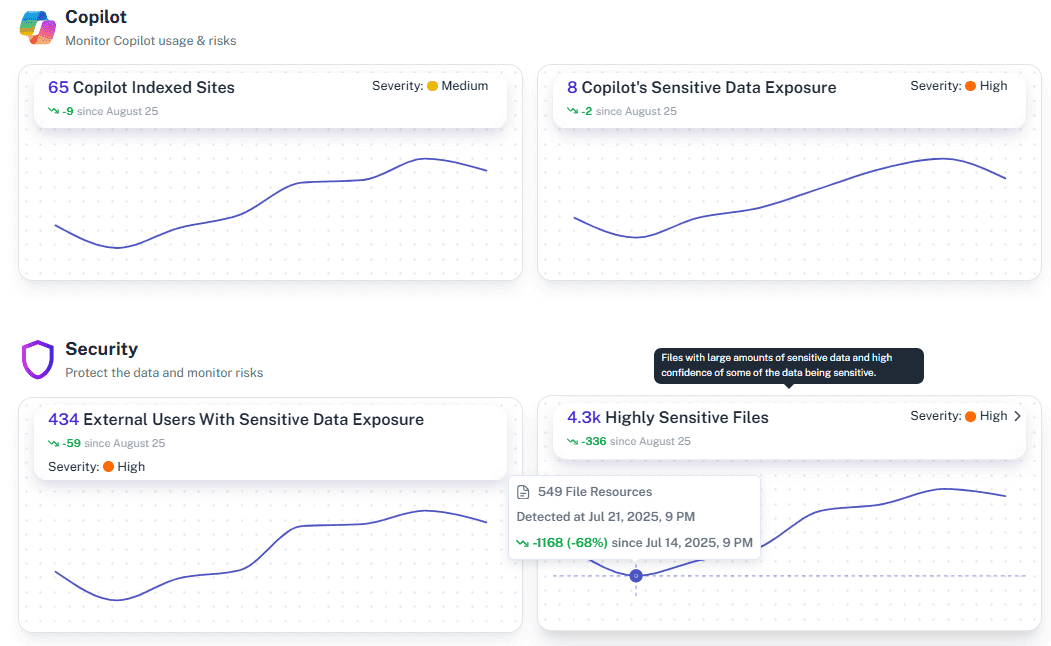
What is the challenge?
Doing It with 1Security
Eliminate the blind spots left by native tools. 1Security delivers the clear, consolidated overview you need for Office 365 OneDrive monitoring, compliance, and risk control.
Unified Visibility
See every OneDrive account, shared file, external user, and permission from a single dashboard — no more bouncing between admin centers.

Real-Time Risk Monitoring
Spot risky behaviors instantly, from “anyone” links to over-privileged or inactive accounts, before they turn into compliance issues.

Context & Compliance
Understand not just that a file is shared, but who has access, how they got it, and what else they can reach. Generate GDPR, HIPAA, and ISO 27001 audit-ready reports in minutes.
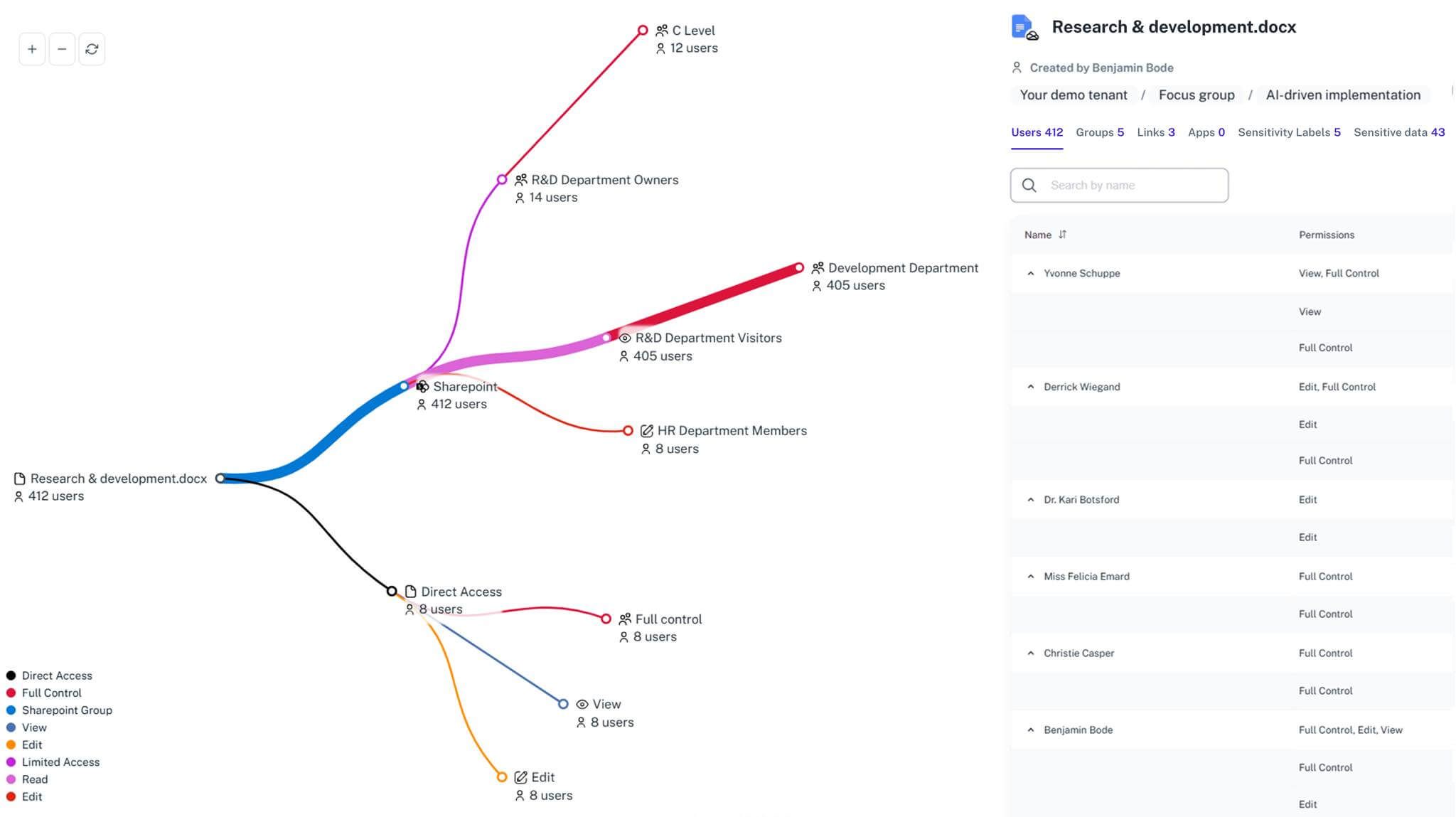
Permission Time Travel
Roll back to a previous safe state with one click, restoring permissions exactly as they looked before an incident.
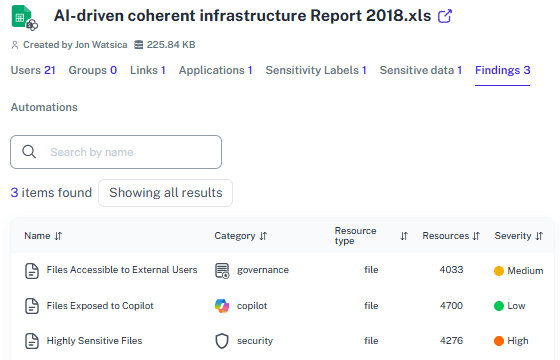
AI & Performance Readiness
See which OneDrive files Copilot might expose, monitor service health, and track usage trends — ensuring secure, optimized adoption of AI.

Solving It with Other Methods
Organizations turn to manual audits, Microsoft’s native dashboards, or third-party apps — but each breaks down in practice: too much manual effort, too many disconnected views, or not enough detail to answer the questions that matter.
Why OneDrive Monitoring Matters?
1Security gives you complete visibility into OneDrive, detects risky sharing in real time, simplifies compliance reporting, and protects sensitive files — so you stay in control instead of buried in audit logs.
"We used to spend days reviewing logs to track OneDrive sharing. Now 1Security flags risky links instantly. Our auditors love the automated reports—and we finally feel in control."
IT Security Manager, European Financial Services Client"When an employee left, we discovered years of confidential files sitting in their OneDrive. With 1Security, we now get alerts before data walks out the door. It’s easy to monitor user activity, select OneDrive details, and provide feedback across departments."
Microsoft 365 Admin, Higher Education Institution"OneDrive used to be our biggest blind spot. With 1Security, we see external shares the moment they happen and can drill into any user’s activity in seconds. Audit prep went from days to minutes."
Head of Information Governance, Healthcare ProviderWho Benefits Most?
1Security supports organizations of all sizes — from highly regulated industries to fast-growing mid-size firms.
Works seamlessly with your ecosystem
1Security connects natively with the tools you already use — giving you full visibility and control without adding complexity.
Frequently asked questions
Everything you need to know about the product.
What about inactive or orphaned OneDrive accounts?
1Security detects inactive users and alerts admins when a user’s OneDrive is still active after offboarding. This prevents sensitive data from being left behind in forgotten accounts.
Can I monitor an individual user’s OneDrive activity?
Yes. You can drill into a user’s OneDrive to see file activity, access data, and last activity date.
How does 1Security track total and active files in OneDrive?
The platform reports on OneDrive activity and usage trends. This gives admins a clear picture of usage, storage, and compliance readiness.
Can 1Security alert me when sensitive files in OneDrive are shared externally?
Yes. 1Security detects risky external sharing in OneDrive — including “anyone with the link” shares — and alerts admins in real time. This gives security teams the chance to remediate exposures before they escalate into compliance issues or breaches.
Does 1Security integrate with Microsoft Graph and audit logs for OneDrive?
Absolutely. 1Security uses Microsoft Graph APIs, admin consent, secret key validation, application permissions, and audit logs to provide accurate monitoring, metrics, and context for OneDrive environments. This enables admins to act quickly with confidence.
Do you support ISO 27001, SOC 2, HIPAA, and GDPR work?
Yes. 1Security maps findings and evidence to common control frameworks, helping organizations demonstrate compliance more efficiently.
Can non-technical stakeholders use it?
Yes. Plain-language reports and read-only views make it easy for compliance, legal, and business stakeholders to see the evidence behind findings without needing admin rights.
Is this only for large enterprises?
No. While designed for complex environments, 1Security is equally valuable for mid-sized organizations running Microsoft 365 or Office 365 that need strong visibility into access, activity, and compliance.
Gain visibility. Ensure compliance. Boost productivity.
Stop guessing who has access to your sensitive data. With 1Security, you gain the visibility, automation, and confidence needed to protect your Microsoft 365 environment.










