Full visibility and control for Microsoft 365.
See who can access what, where sensitive data lives, and how permissions change over time — so you stay compliant, secure, and AI-ready.



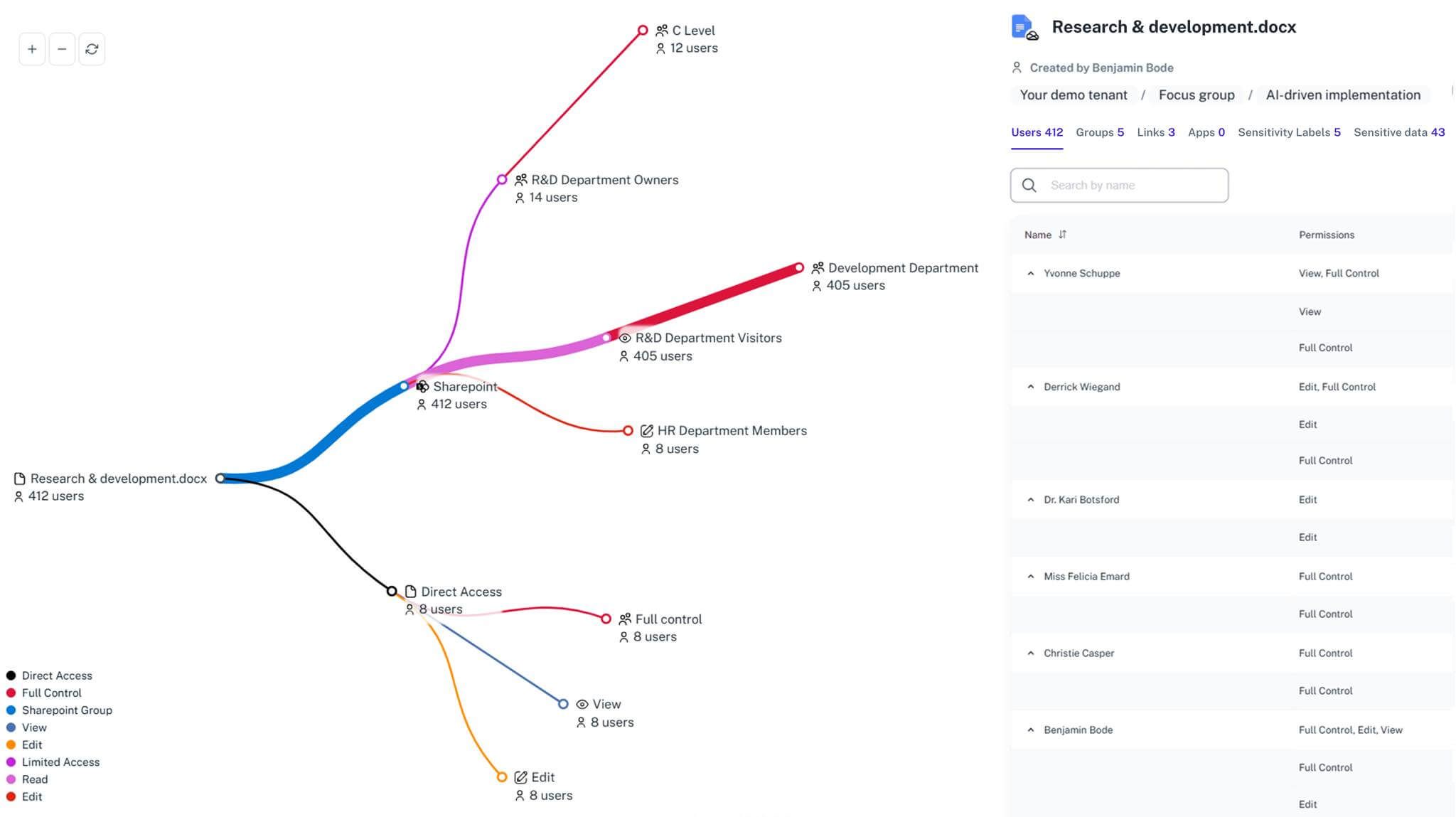
Confidently scale M365 and Copilot
Grow collaboration and adopt AI without growing risk.
Crystal-clear access
See who can access what—fast—across SharePoint, Teams, OneDrive.
Safer sharing by default
Find and retire “Anyone” links, expire risky shares, and prevent oversharing without slowing work down.
AI-ready collaboration
Ensure Copilot and apps only see what they should with exposure checks and guardrails.
One platform. Four superpowers.
Tenant-wide visibility, monitoring, investigations, and governance in one place.
Visibility & Reporting
Tenant-wide access map and exportable, audit-ready reports.
Monitoring & Alerts
Track share and permission changes with actionable, low-noise alerts.
Forensics & Access Logs
Reconstruct who had access, when, and why — before and after incidents.
Automations & Governance
Expire risky links, remove excessive access, and schedule owner recertifications.

Intuitive access intelligence for data-driven teams.
Cut through M365 noise with insights that show exactly who can access what — no manuals, no confusion, just answers.

See 1Security in action
Purpose-built workspaces for monitoring, auditing, reporting, and inventory management.
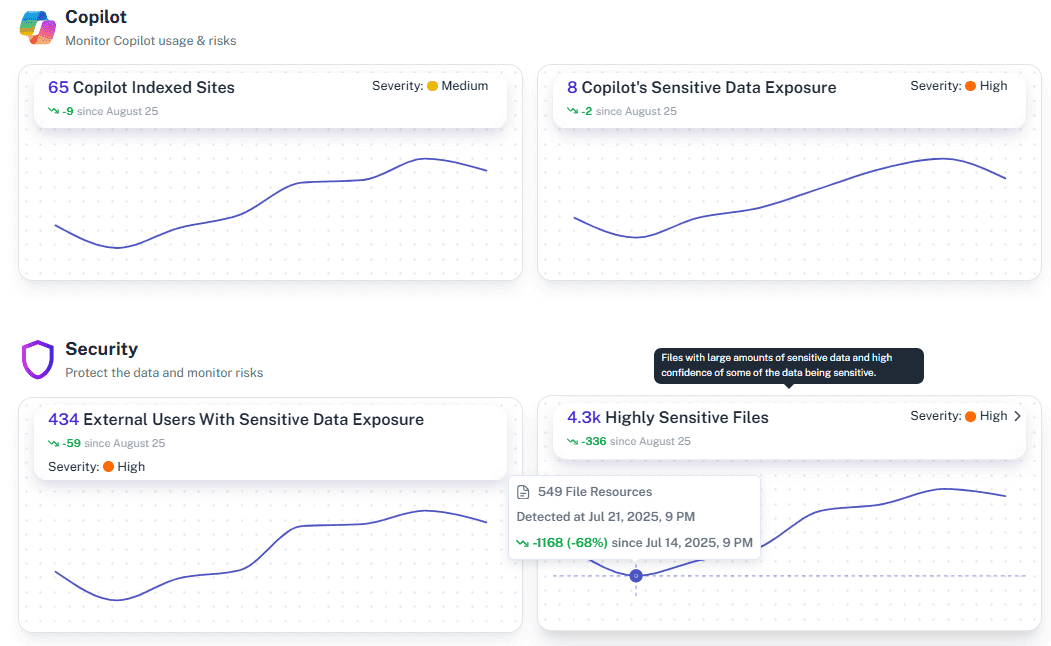
Microsoft 365 Monitoring Tool
Live stream of changes with risk context.

Microsoft 365 Audit Tool
Evidence packs for auditors in minutes.

Office 365 Reporting
On-demand and scheduled CSV, PDF, and API reports.
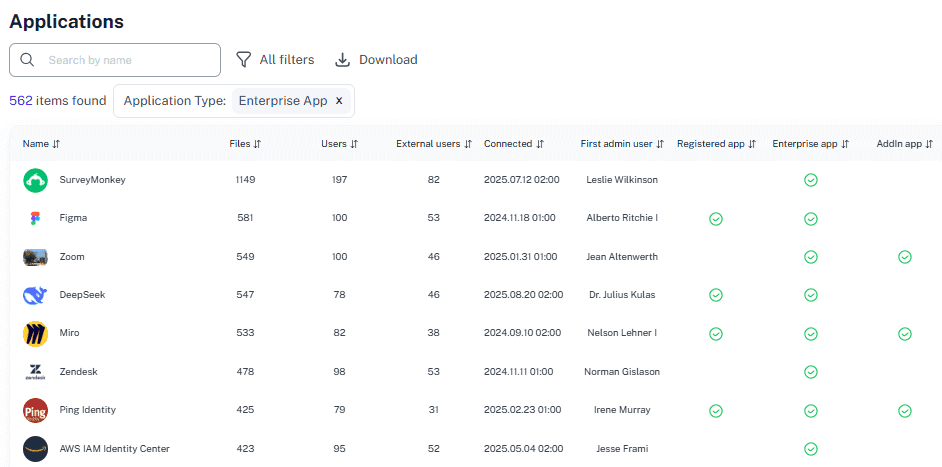
Microsoft 365 Inventory Tool
One source of truth for sites, teams, owners, and guests.
Solving real problems
Common scenarios your teams face — with workflows that prevent oversharing, reduce sprawl, and accelerate audits.
Proof it works
Quantified outcomes and recognizable logos build confidence that your governance program will deliver value from day one.
- 20x
faster access reviews
- 75%
less time on manual audits
- 8×
quicker investigations
- 100m+
files scanned
- 100k+
users scanned
Security You Can Trust
1Security is built with enterprise-grade protection. We are ISO 27001 certified, fully GDPR compliant, and host all customer data in secure European data centers. Your sensitive information stays private, protected, and audit-ready.

Works seamlessly with your ecosystem
1Security connects natively with the tools you already use — giving you full visibility and control without adding complexity.
Frequently asked questions
Everything you need to know about the product and billing.
What makes 1Security different from Microsoft Entra ID (Azure AD)?
Microsoft provides basic identity and access controls, but lacks real visibility into who actually has access to which files, sites, and data. 1Security fills this gap with a detailed, user-friendly map of permissions across Microsoft 365, including sensitive data locations and historical changes so you can govern AI and human access confidently.
Can 1Security replace our existing DLP or compliance tools?
No – it complements them. Tools like Microsoft Purview or Varonis protect data but require you to guess what should be protected. 1Security shows you where sensitive data is and who has access before you set policies. It also enhances your access management IAM strategy by providing visibility into digital identities and supporting regulatory compliance requirements.
Can 1Security track external guest access across the inventory?
Yes. Guest accounts and external users are visible in the unified inventory, so you can see who still has access and remove them if needed.
Can it track historical audit data?
Yes. 1Security retains audit logs with timestamps and tracks key changes such as group membership, sharing link creation, and permission state history — with time-stamped records for audits.
Can it support AI readiness assessments?
Yes. 1Security analyzes permissions, labels, and exposure paths to verify controls and identify risks for safe Copilot adoption. It identifies data security risks and creates actionable recommendations so your organization can adopt Copilot safely and meet privacy standards set by the European Union.
Can non-technical stakeholders use it?
Yes. Plain-language reports and read-only views make it easy for compliance, legal, and business stakeholders to see the evidence behind findings without needing admin rights.
Does it support Microsoft Copilot readiness?
Yes. 1Security’s audit features reveal sensitive data and oversharing that could be exposed by Copilot, ensuring labels, access boundaries, and policies are aligned before rollout.
Does 1Security integrate with advanced security features like privileged identity management and conditional access policies?
Yes. 1Security works alongside privileged identity management (PIM), conditional access policies, and access policies in Microsoft 365 and Azure AD. It provides visibility into privileged roles, helps enforce access policies, and supports granular control over who can access sensitive resources.
Do you support ISO 27001, SOC 2, HIPAA, and GDPR work?
Yes. 1Security maps findings and evidence to common control frameworks, helping organizations demonstrate compliance more efficiently.
Take control of Microsoft 365 access today
Stop guessing who has access to your sensitive data. With 1Security, you gain the visibility, automations, and confidence needed to protect your Microsoft 365 environment.










