Microsoft 365 reporting guest access
Your Microsoft 365 has ghosts: ex-vendors, forgotten freelancers, mystery emails and employees that left over 3 years ago that still have SharePoint access. 1Security spots every guest user immediately, turning spooky oversharing into clean, verified access reports your auditors can trust.
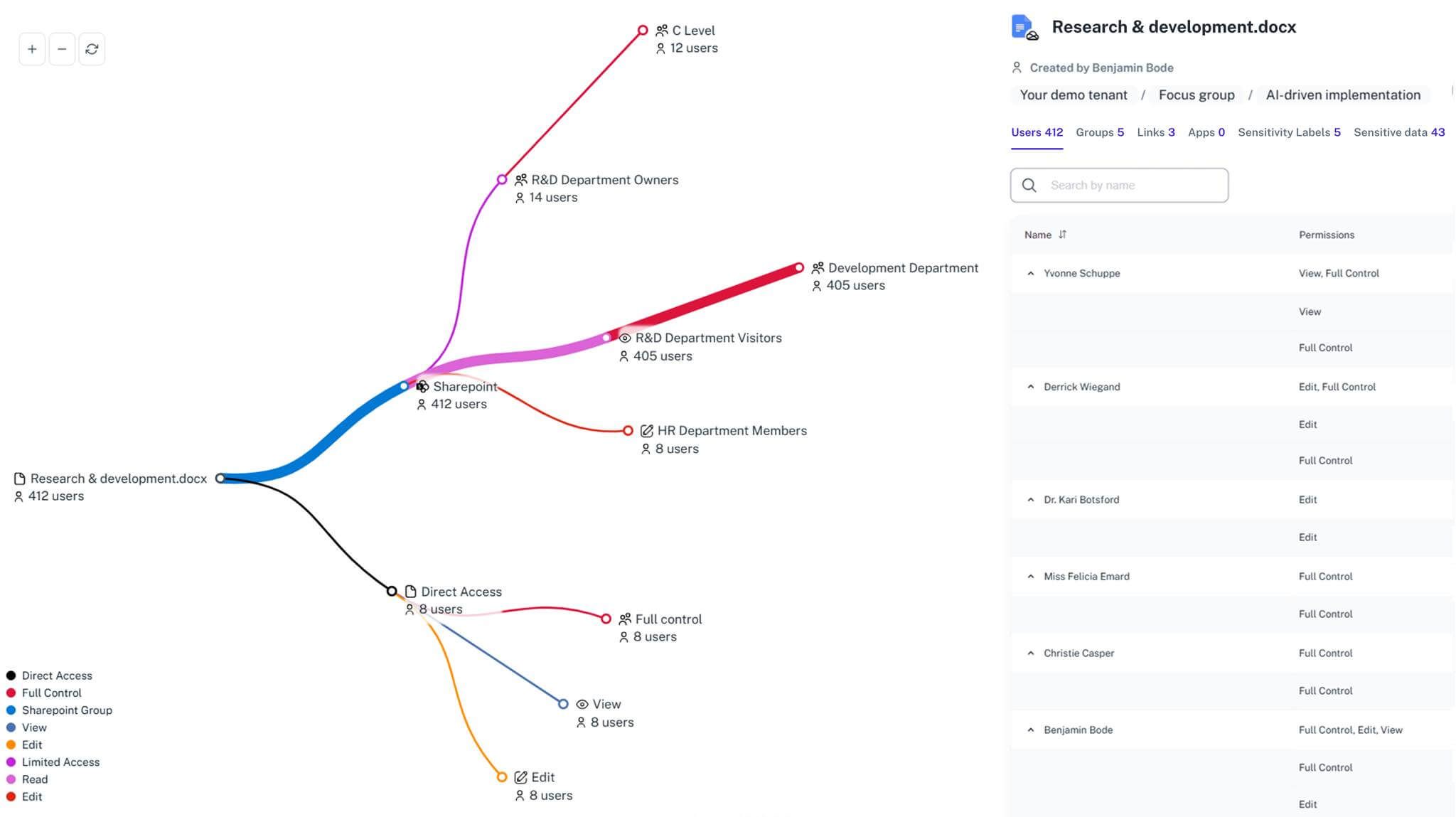
What is the challenge?
Doing It with 1Security
Eliminate uncertainty around guest access. 1Security delivers complete visibility into guest access across Microsoft 365, showing which guest users are inside, what they can reach, and how their permissions change over time.
Unified Guest Access View
All guest accounts, external users and shared links appear in one 1Security dashboard integrated with Microsoft Entra. No more jumping between portals or Power BI reports to piece together external access.

Automated Reporting and Exportable Evidence
Generate guest access reports with timestamped evidence for audits, certifications and access reviews. Reports include comprehensive identity data and verifiable user attributes necessary for auditing reasons.

Permission Change Tracking
Every permission change is logged with complete forensic context: WHO made the change, FROM WHERE, WHEN. This detailed audit trail enables rapid incident investigation and proves to auditors that unauthorized changes are detectable and recoverable.

Sensitive Data Context
Overlay guest activity with data sensitivity levels from Microsoft Purview to immediately highlight high-risk exposures or unauthorized users.
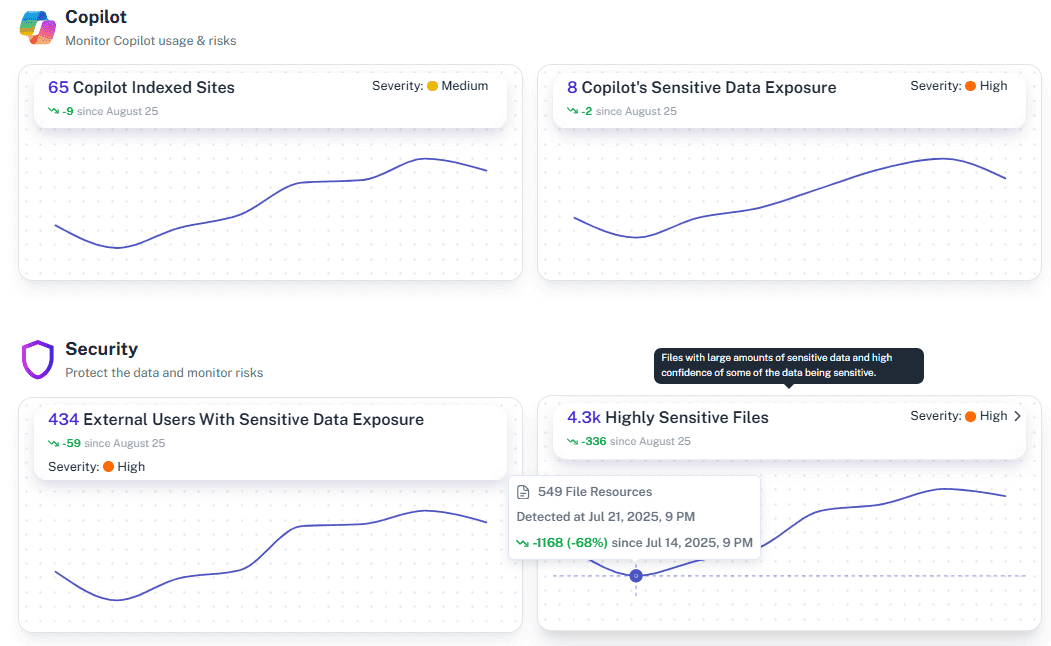
Anomaly Alerts
Receive alerts when new guests gain access to sensitive sites or when dormant accounts and external guest users become active again.
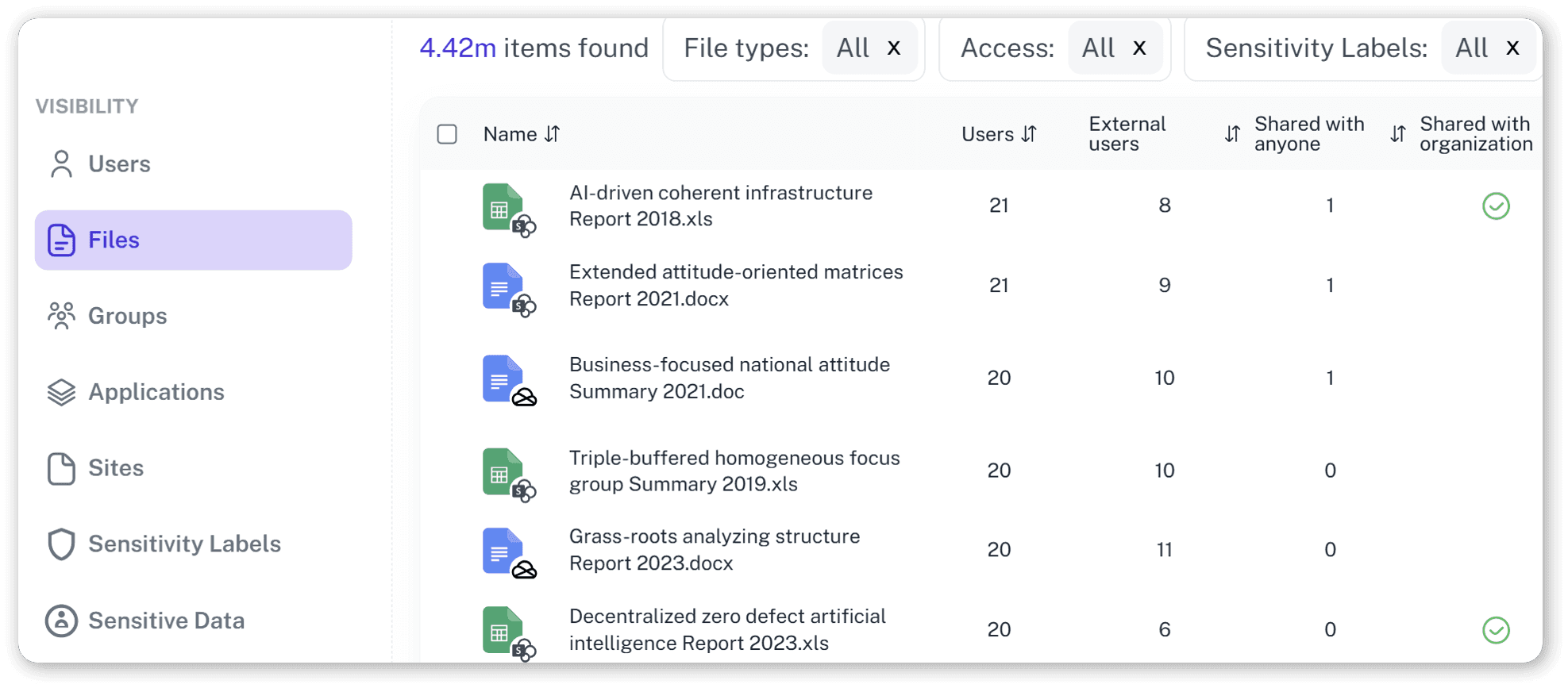
AI Safety Checks
Get full control and visibiliy over Copilot’s and other AI tools data access and ensure itstays limited to approved data, keeping guests from seeing sensitive content.
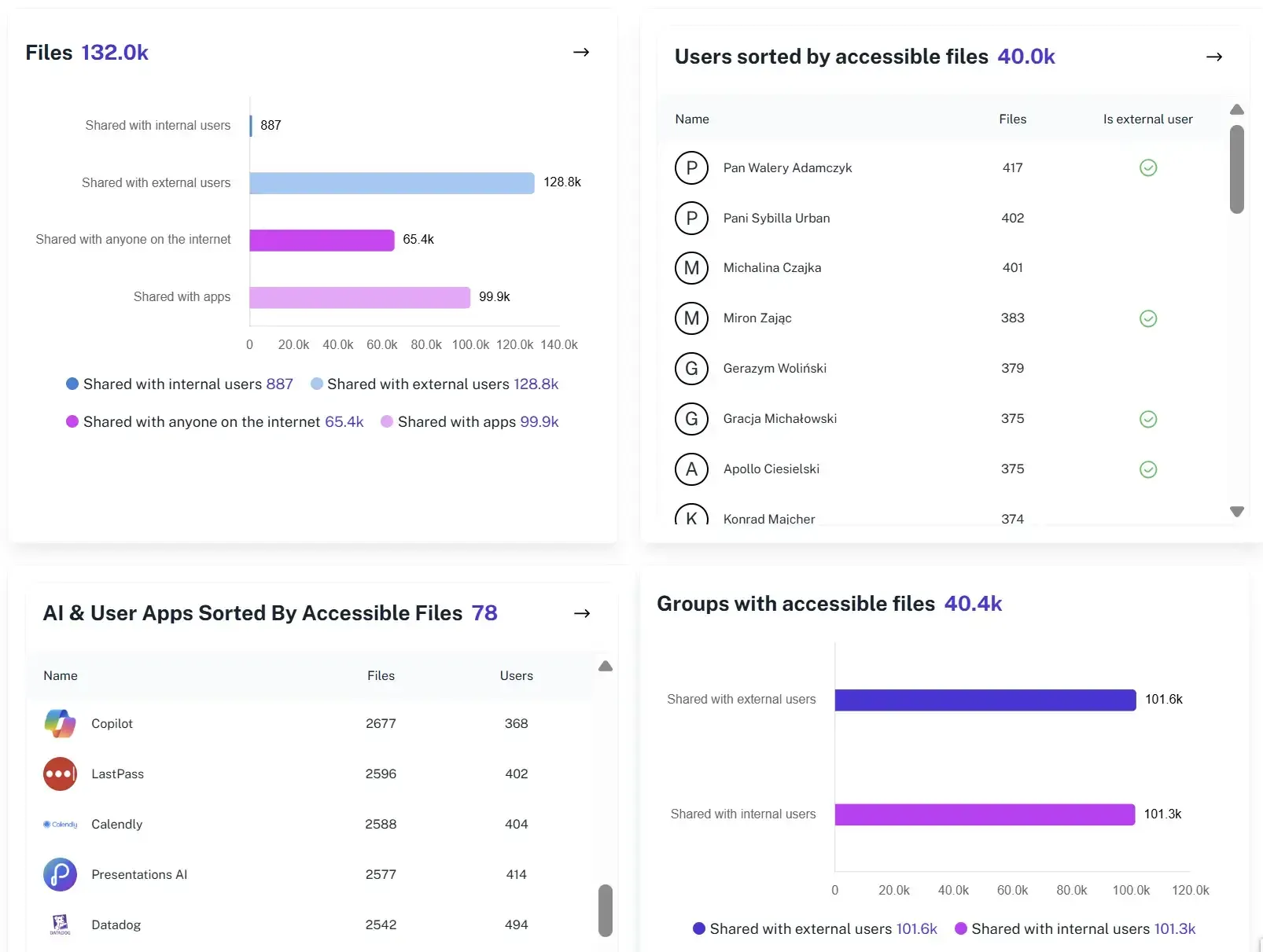
Audit-Ready Snapshots
Generate historical access states using a time-based report to prove compliance or reconstruct incidents, adhering even to NIS 2 standard. These snapshots include necessary scopes for forensic clarity.
Solving It with Other Methods
Organizations try to manage Microsoft 365 guest access reporting in a few ways but none are ideal.
Why Guest Access Reporting Matters?
1Security gives every organization the visibility it needs to manage guest users safely, comply with regulations and maintain data security across the Microsoft 365 tenant.
"Before 1Security, tracking guest users and external access across Microsoft 365 was chaos. Now we run clear reports in minutes – every guest account is verified before audit time."
Compliance Manager, Global Insurance Firm"With 1Security’s guest access reporting, we finally know who our external users are, what they can reach and when permissions change – perfect evidence for ISO and GDPR reviews."
Director of IT Compliance, Public University"1Security gives us full visibility into guest accounts across Teams and SharePoint. We can spot inactive users, revoke access fast and prove control during audits."
Microsoft 365 Admin, Higher EducationWho Benefits Most?
1Security supports organizations of all sizes — from highly regulated industries to fast-growing mid-size firms.
Works seamlessly with your ecosystem
1Security connects natively with the tools you already use — giving you full visibility and control without adding complexity.
Frequently asked questions
Everything you need to know about the product.
What does 1Security’s Microsoft 365 reporting guest access feature cover?
It includes all Microsoft 365 external guest users, shared links and apps across SharePoint, Teams and OneDrive with detailed permission and access context.
Can 1Security detect inactive or orphaned guest accounts?
Yes. The platform flags inactive guest users, dormant sessions and accounts with no recent activity so you can revoke access safely using Entra ID or conditional access policies.
How often are guest access reports updated?
Reports update continuously within the Microsoft 365 environment reflecting every change in real time so admins always have an accurate overview.
Does it integrate with Microsoft Purview or Copilot?
Yes. 1Security overlays Purview sensitivity labels and highlights where Copilot or Office apps might expose sensitive tenant data to guest users.
Can 1Security show how guest access changes over time?
Yes. 1Security tracks historical access states and permissions so you can review past configurations and demonstrate full control during audits.
Do you support ISO 27001, SOC 2, HIPAA, and GDPR work?
Yes. 1Security maps findings and evidence to common control frameworks, helping organizations demonstrate compliance more efficiently.
Can non-technical stakeholders use it?
Yes. Plain-language reports and read-only views make it easy for compliance, legal, and business stakeholders to see the evidence behind findings without needing admin rights.
Is this only for large enterprises?
No. While designed for complex environments, 1Security is equally valuable for mid-sized organizations running Microsoft 365 or Office 365 that need strong visibility into access, activity, and compliance.

Gain visibility. Ensure compliance. Boost productivity.
Stop guessing who has access to your sensitive data. With 1Security, you gain the visibility, automation, and confidence needed to protect your Microsoft 365 environment.










