Microsoft 365 Security Audit
You didn’t choose this career to spend late nights hunting through logs and stitching together CSVs. You’ve got better things to focus on. We don’t. 1Security turns every audit into a non-event with automatic visibility, historical insights, and instant comprehensive evidence.
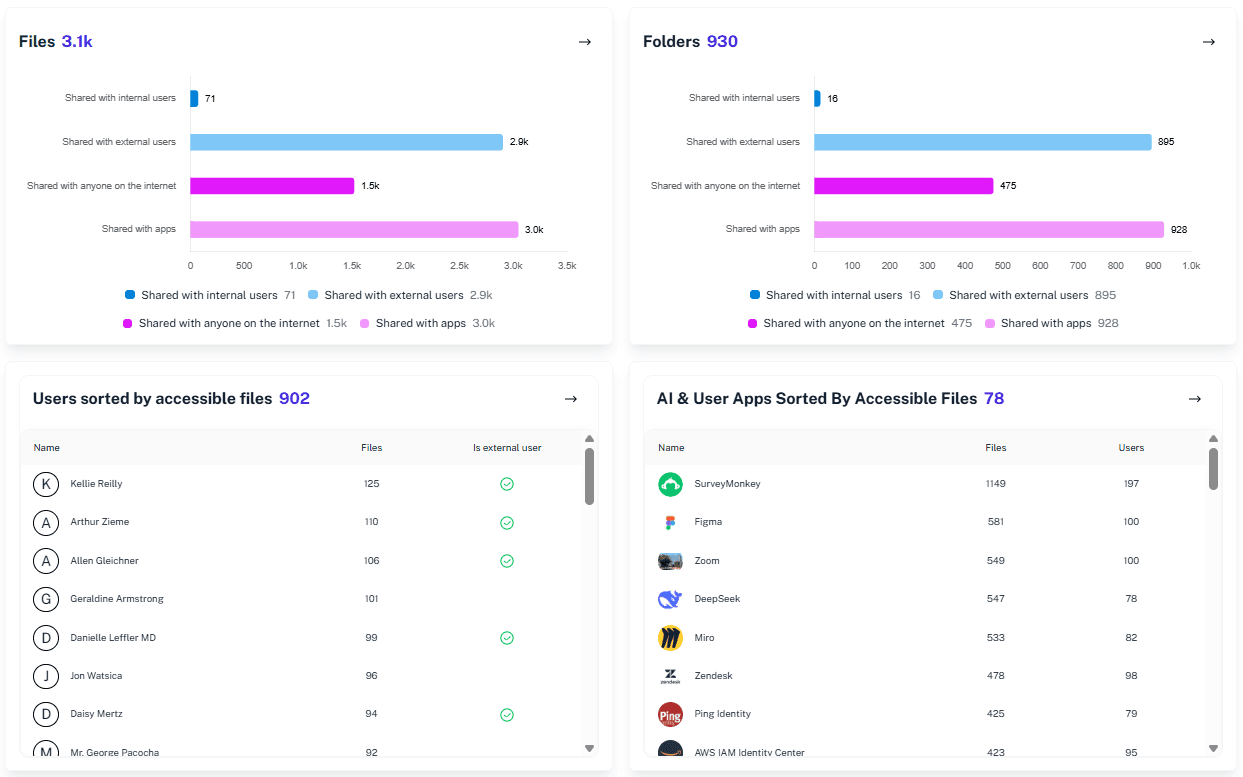
What is the challenge?
Doing It with 1Security
Eliminate uncertainty in your Microsoft 365 security audit. 1Security delivers clear, continuous visibility into access, permissions and data exposure so you can prevent incidents before they are discovered during an audit.
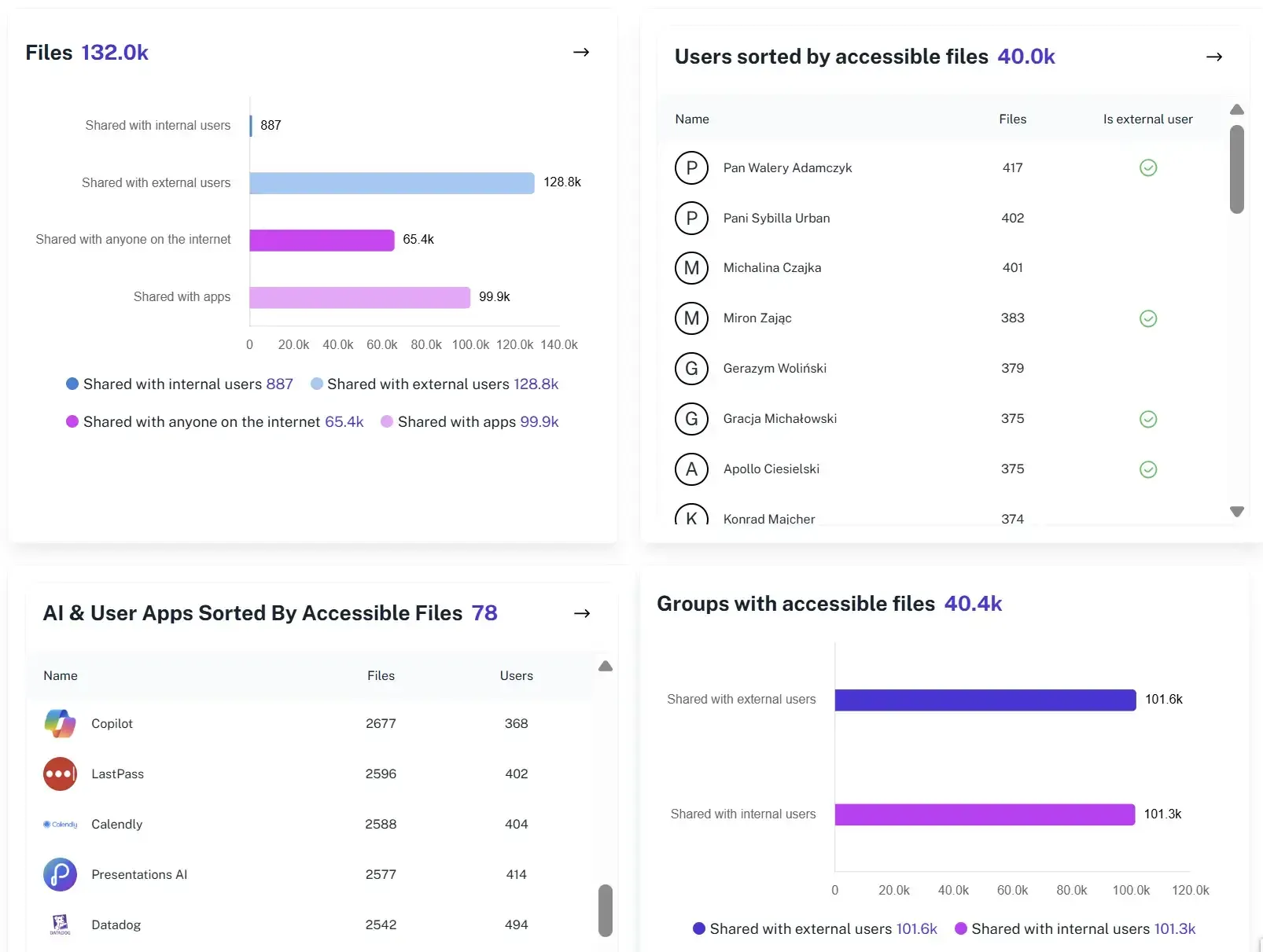
Single source of truth for Microsoft 365
Gain complete visibility and control across SharePoint, OneDrive, Teams and Entra ID. See every permission, understand its context and manage access with confidence.
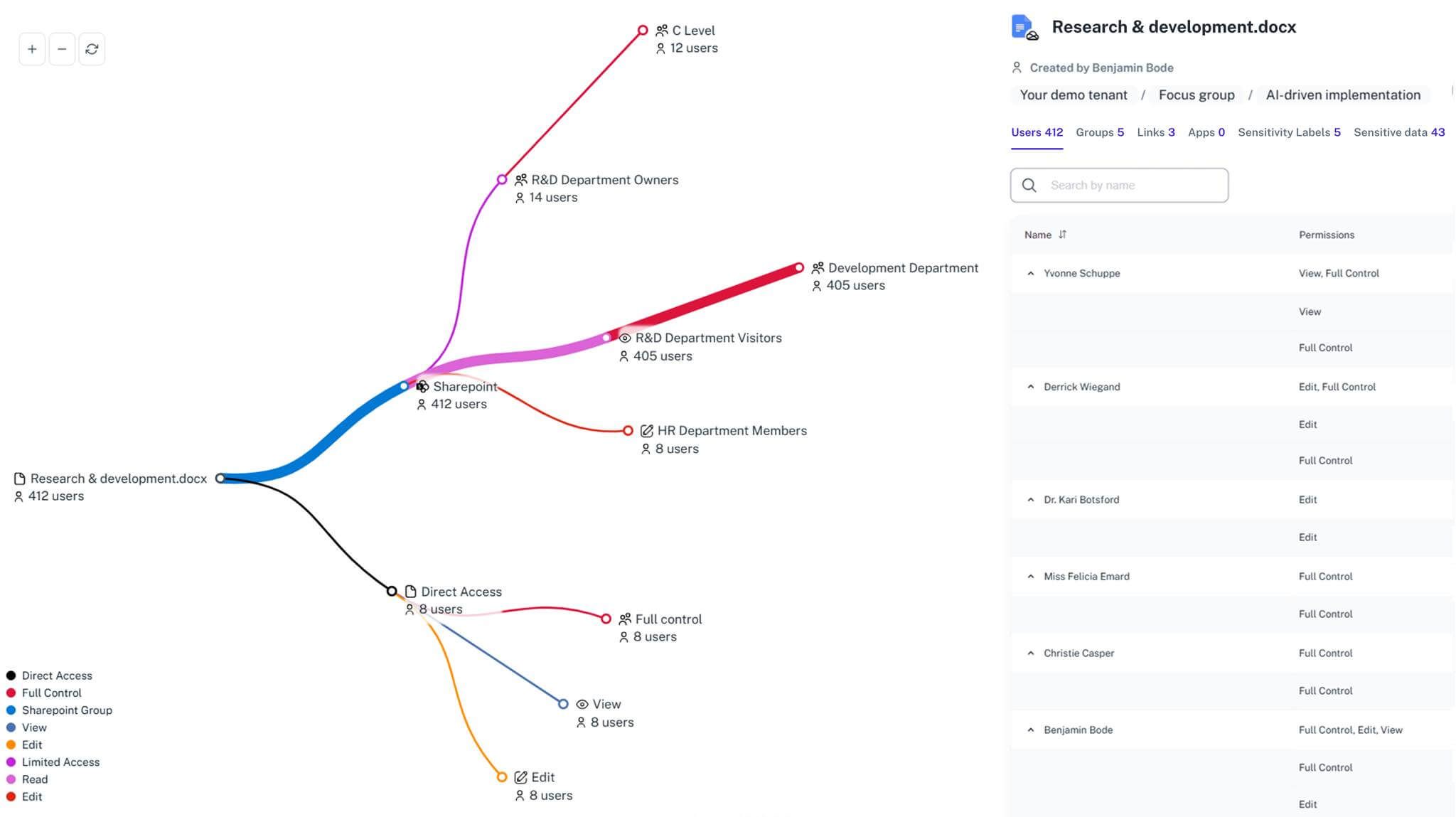
Sensitive data correlation
Map sensitive data to their exact permission paths and external exposure to spot oversharing or compliance risks early. This strengthens data protection and supports regulatory requirements.

Continuous evidence collection
1Security tracks every permission change in real time and keeps a historical record and audit logs ready for any audit or investigation.

Audit-ready reporting
Generate exportable, time-stamped evidence packs for auditors in minutes. Every permission, every change, every file is verified to support compliance frameworks.
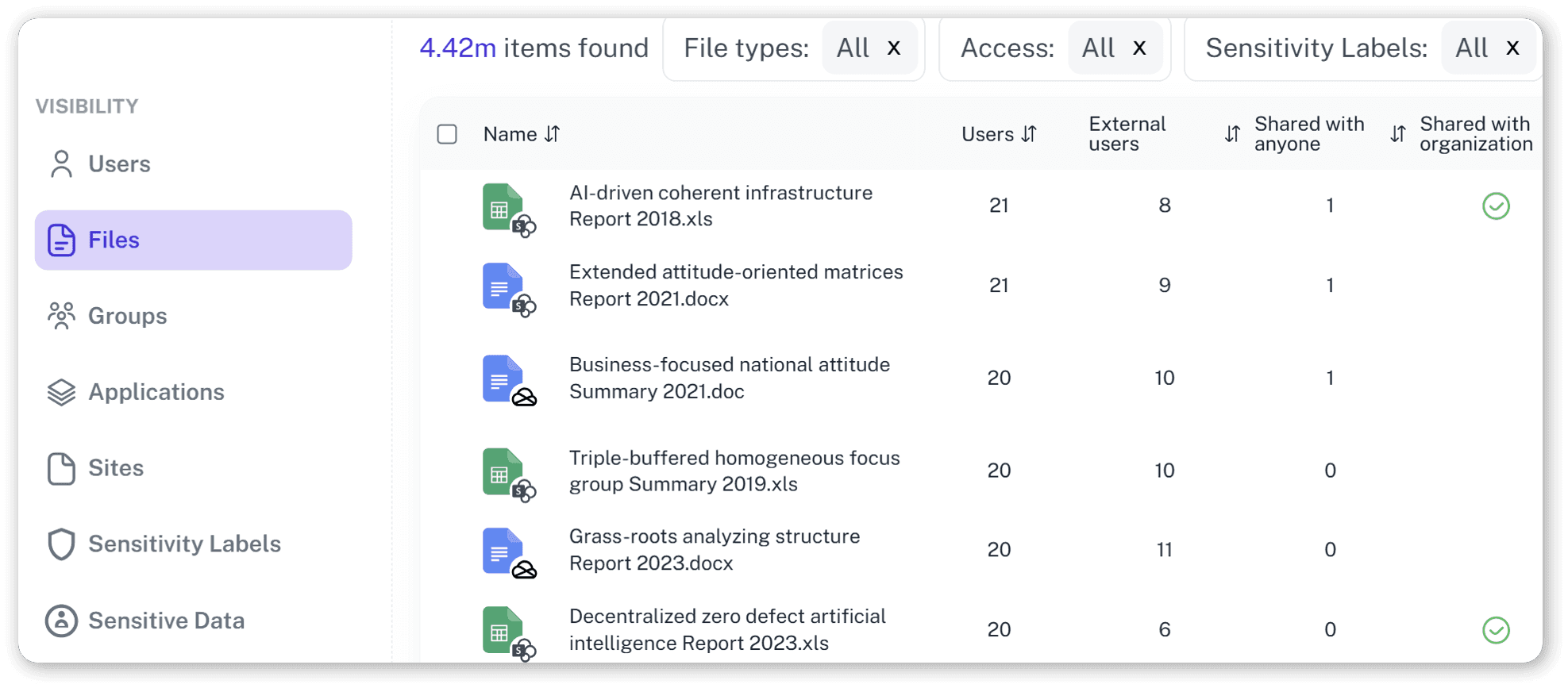
Incident prevention insights
Detect unusual sharing behavior, dormant accounts and policy violations before they turn into security incidents or data breaches.
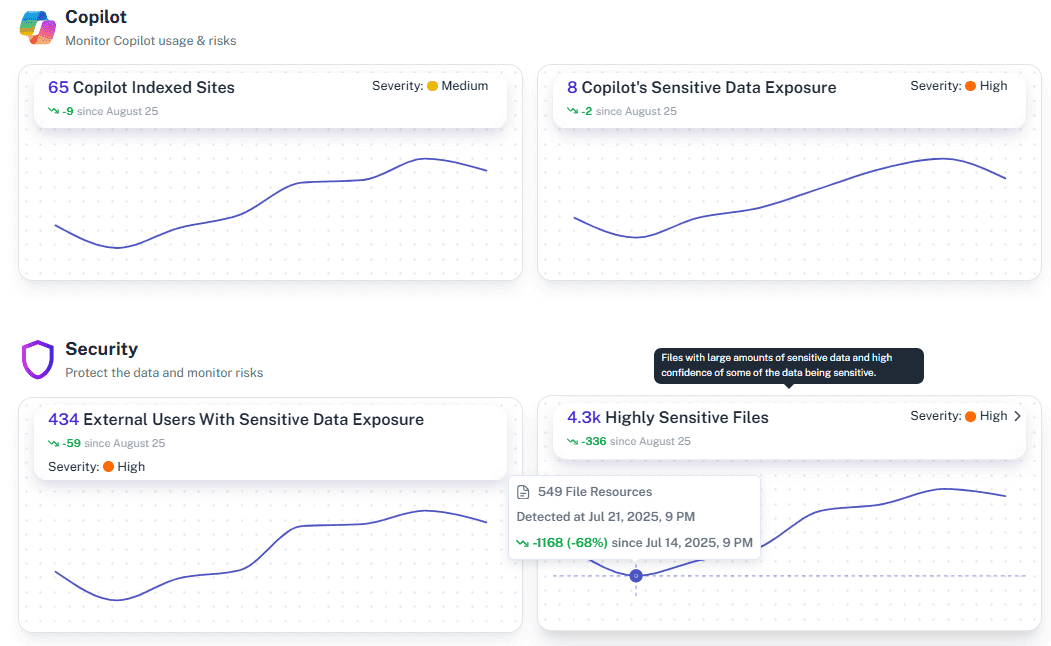
AI and Copilot readiness
Validate that Microsoft Copilot and other connected applications can only see approved data, supporting safe AI adoption and threat detection.
Advanced threat detection
1Security uses security monitoring and threat intelligence to continuously monitor potential threats and identify vulnerabilities across your environment.
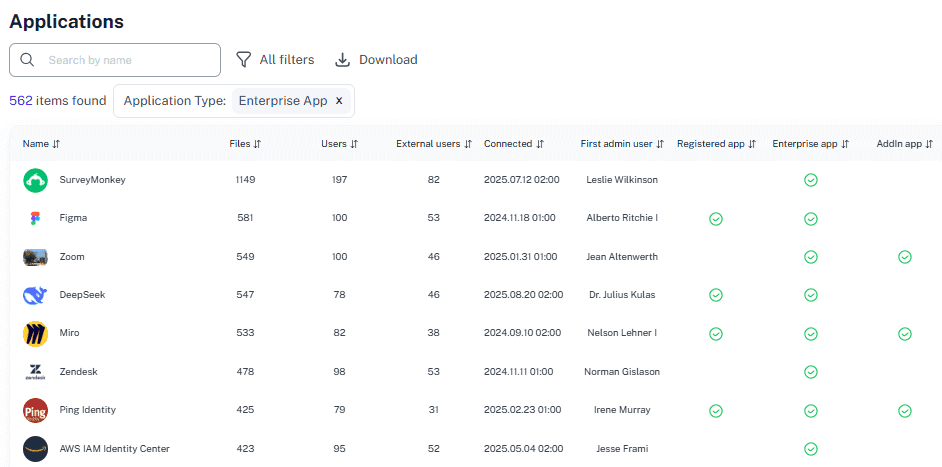
Solving It with Other Methods
Organizations often try to handle Microsoft 365 security audits manually or with limited native tools. It works in theory but breaks in practice once the environment scales.
Why Microsoft 365 Security Audit Matters?
1Security gives you continuous visibility into who can access what, how data moves and where risk originates. It helps organizations detect oversharing, monitor privilege changes and prevent incidents that would otherwise surface during audits.
"Before 1Security, preparing for audit reviews meant weeks of spreadsheets. Now we generate evidence packs in minutes. Auditors appreciate the clarity."
Compliance Manager, Global Insurance Firm"With 1Security’s reporting, we can finally prove control. Every permission change is tracked, reports are exportable and there are no surprises during ISO or GDPR reviews."
Director of IT Compliance, Public University"With 1Security’s monitoring, we finally know which accounts and sites are active and which should be archived, all visible in a single dashboard."
Microsoft 365 Admin, Higher EducationWho Benefits Most?
1Security supports organizations of all sizes — from highly regulated industries to fast-growing mid-size firms.
Works seamlessly with your ecosystem
1Security connects natively with the tools you already use — giving you full visibility and control without adding complexity.
Frequently asked questions
Everything you need to know about the product.
What does a Microsoft 365 security audit include?
It reviews access controls, permissions and data sharing across Microsoft 365 to identify vulnerabilities, data breaches and compliance gaps.
How does 1Security simplify the audit process?
1Security unifies permission, user access and data visibility into one platform, automatically tracking changes, continuously monitoring and generating audit evidence.
Can 1Security detect risky file sharing?
Yes. It identifies links, guest accounts and shared sites that expose sensitive data or critical data to unauthorized users.
How often should a Microsoft 365 security audit be done?
Continuous monitoring is ideal. 1Security automates this process, replacing manual audits with ongoing oversight to strengthen security posture.
Does it help with compliance certifications?
Yes. 1Security provides ISO, GDPR and HIPAA-ready reports that simplify documentation, support compliance frameworks and prove adherence to regulatory requirements.
Do you support ISO 27001, SOC 2, HIPAA, and GDPR work?
Yes. 1Security maps findings and evidence to common control frameworks, helping organizations demonstrate compliance more efficiently.
Can non-technical stakeholders use it?
Yes. Plain-language reports and read-only views make it easy for compliance, legal, and business stakeholders to see the evidence behind findings without needing admin rights.
Is this only for large enterprises?
No. While designed for complex environments, 1Security is equally valuable for mid-sized organizations running Microsoft 365 or Office 365 that need strong visibility into access, activity, and compliance.

Gain visibility. Ensure compliance. Boost productivity.
Stop guessing who has access to your sensitive data. With 1Security, you gain the visibility, automation, and confidence needed to protect your Microsoft 365 environment.










